Saturday, July 26, 2014
Skype Voice recording
In order to record important Skype calls with the consent of the other party, go to the website http://voipcallrecording.com/ and download the free MP3 Skype Recorder tool. The file will be downloaded in a .msi file format.
Once it is downloaded onto your machine you just need to open Skype up and make a call. Once the call is in progress, select the "ON" button. In the lower left hand corner, it will let you know the tool is recording and it will place the recorded file inside the pre-selected folder.
Wednesday, May 21, 2014
Spam
Here is a site you can use to reduce some spam coming into your inbox.

Spam worldwide tends to advertise a certain range of goods and services irrespective of language and geography. Additionally, spam reflects seasonal changes, with advertisements for Christmas items and car heaters being replaced by air conditioner advertising in the summer.

Remember, when dealing with spam:
· Do not click web links inside spam.
· Do not load the images inside spam.
If you do any of the above, then this will notify the
spammer that someone is checking emails at that email address and you will get
more spam. By default, when you select an email and Outlook opens it in the
preview pane it does not load images. You have to click to tell Outlook to load
images, do not do this. The preview pane is the pane that shows the email
message on the right hand side.
Also, you can select the email and click ignore in the top
left. This will ignore additional emails in the future.

Here is a website that can provide you with examples of
spam.
Spam worldwide tends to advertise a certain range of goods and services irrespective of language and geography. Additionally, spam reflects seasonal changes, with advertisements for Christmas items and car heaters being replaced by air conditioner advertising in the summer.
Spammers constantly extend the range of their offers and are always searching for new ways of attracting unwary users. The list of spam categories is growing. The share of “new” categories in spam traffic is insignificant, though certain trends are quite evident when spam categories are broken down. Nevermore so than in the most widespread types of spam:
However, when averaged out over the course of the year, 50% of spam fall into the following categories:
1. Adult content
2. Health
3. IT
4. Personal finance
5. Education and training
If you see web links in an email, hover over the link, but
do not click. If the link inside the email tells you it is going to one site,
then when you hover over the link and it has a different website than what you
see in the email; this is a clear indicator that it is a malicious link.

Sunday, March 2, 2014
Target getting hacked and creating a better password
Dell released a full report on how Target got hacked. They lost around 40 million debit and credit card accounts. Along with this loss, they also lost 70 million Names, home address email addresses and phone numbers. This is a large corporation and because of its size it was targeted by hackers. In order to summarize the report, hackers were able to gain access to Target's internal server by elevating a built-in account on their deployed Point of Sales (PoS) system. Once they gained access they deployed a piece of malware that skimmed memory in the PoS system. Once it skimmed the memory, it could sniff out credit card numbers and drop the data on a server they deployed inside the server. Every once and a while they would dump this credit card data because the server would fill up. It was amazingly fast to how quick it would fill up. They reported that they were dumping the server every few hours or so.
The username and password is as follows: Username: Best1_user Password: BackupU$r. Pretty simple, right? It has uppercase, symbols and numbers. Although, the problem is that the password is so simple and the password even contains part of the username. As you all may know, a good password contains letters, numbers, symbols and is longer than 8 characters. The problem here is that you aren't supposed to use the username anywhere in the password. Replacing letters like S with $ still counts as using the username within the password. The password should have been a passphrase instead of a pass"word". Something of the nature like "This1IsTheBest_user" would have sufficed.
You can also take things a step further by using letters, symbols, numbers, longer than 8 characters and don't use ANY words from the dictionary. So used made up words from merging different words together. Say you own a Jeep and a Caterpillar tractor, you could use the password "JeCaterepPiller1970!". Lets say 1970 is the year the tractor was made. Now you have a password that meets all of these criteria:
Don't forget that you can include periods in the middle between words, which would help you satisfy your symbol requirements. So we can use "Jeep.Caterpiller1970!" and this will suffice as well. Some may argue that you should not use numbers in sequence because most people use their birthyear, which makes the number portion guessable. Some may also use the year they got the dog or the year their Jeep is. (also tractor) Try to avoid this obviousness and use numbers that don't relate to anything you own. Some may even try "Jeep.Caterpiller70!", but this doesn't solve the problem. A hacker can easily figure out your birthyear is 1970 and try 70 at the end of your password.
If you are having issues trying to determine a good password and want to know how well it stands up against a hacking tool, try this website out: http://www.passwordmeter.com/.
If you will notice, this website's password checker is also under the GNU license, so you can download it and use it in your business for free!
I have attached the Dell report from Krebsonsecurity's blog. I would recommend taking a glance/read through his stuff, too.
http://krebsonsecurity.com/wp-content/uploads/2014/01/Inside-a-Targeted-Point-of-Sale-Data-Breach.pdf
The username and password is as follows: Username: Best1_user Password: BackupU$r. Pretty simple, right? It has uppercase, symbols and numbers. Although, the problem is that the password is so simple and the password even contains part of the username. As you all may know, a good password contains letters, numbers, symbols and is longer than 8 characters. The problem here is that you aren't supposed to use the username anywhere in the password. Replacing letters like S with $ still counts as using the username within the password. The password should have been a passphrase instead of a pass"word". Something of the nature like "This1IsTheBest_user" would have sufficed.
You can also take things a step further by using letters, symbols, numbers, longer than 8 characters and don't use ANY words from the dictionary. So used made up words from merging different words together. Say you own a Jeep and a Caterpillar tractor, you could use the password "JeCaterepPiller1970!". Lets say 1970 is the year the tractor was made. Now you have a password that meets all of these criteria:
- Longer than 8 characters
- Capital Letters
- Numbers
- Symbols
- Not consisting of all dictionary words
Don't forget that you can include periods in the middle between words, which would help you satisfy your symbol requirements. So we can use "Jeep.Caterpiller1970!" and this will suffice as well. Some may argue that you should not use numbers in sequence because most people use their birthyear, which makes the number portion guessable. Some may also use the year they got the dog or the year their Jeep is. (also tractor) Try to avoid this obviousness and use numbers that don't relate to anything you own. Some may even try "Jeep.Caterpiller70!", but this doesn't solve the problem. A hacker can easily figure out your birthyear is 1970 and try 70 at the end of your password.
If you are having issues trying to determine a good password and want to know how well it stands up against a hacking tool, try this website out: http://www.passwordmeter.com/.
If you will notice, this website's password checker is also under the GNU license, so you can download it and use it in your business for free!
I have attached the Dell report from Krebsonsecurity's blog. I would recommend taking a glance/read through his stuff, too.
http://krebsonsecurity.com/wp-content/uploads/2014/01/Inside-a-Targeted-Point-of-Sale-Data-Breach.pdf
Thursday, February 27, 2014
DropBox's Terms of Service (ToS) change
A little while ago, DropBox changed their terms of service to update it with a few things. One of them being government taps. Lots of companies and consumers are concerned with the NSA sniffing data they shouldn't be snooping in on. As apart of this concern, DropBox has released a new agreement for their users. They have sent emails to their current users that is as follows as below (part of it):
If you click the link "Government Data Request Principles", then you will notice near the bottom it states the below image:
"Governments should never install backdoors into online services or compromise infrastructure to obtain user data".
This is great news because this means the NSA cannot install backdoor taps into DropBox in order to clamp down on people who may be using DropBox for legit reasons. If you upload just normal documents, they COULD sniff it and just read what it contains. This isn't right because people have a sense of privacy when they do this and by installing backdoors and reading this content it breaks that sense of privacy.
Of course this doesn't apply to people who use DropBox for illegal reasons. The government can still file a government subpoena and gain access to your data. DropBox has to provide them with the data because of the subpoena.
Monday, February 24, 2014
Information gathering
A lot of people think that Hacking or Cracking is the only way to get digital data that is sensitive, but in reality there are many other methods. Social engineering, Dumpster diving, etc. are many other ways to get information the public was never meant to see.
Social engineering is simply making a phone call, knowing the right points of contacts and making sure you know what information you want. Kevin Mitnick was the famous hacker who used this method to gain usernames and passwords from people. http://en.wikipedia.org/wiki/Kevin_Mitnick
An example is as follows, a local IT member gets a call for a password reset from a person who is posing to work with the corporation. Now, because the company is so large, this IT person does not know everyone and cannot recognize their voice. Let's say this hacker starts a casual conversation with the IT person and starts talking about politics or the game that happened the night before. They could, also, say they need access to their account, immediately, for an important meeting. Once the IT person resets their password and lets them know it, then you have successfully gained access to an account you weren't supposed to have access to. Let's say they just reset it and never gave you the password, but you know through research that when they reset passwords it usually consists of some facets of their email address and something else you already know, which makes it easy to gain access to their password and account.
Many companies simply throw out information such as Health information or Military information in the trash. They don't shred this information or do anything to destroy this sensitive information. Some may even just dump it out back after they empty the office's trash cans. This leaves the data open and vulnerable to prying eyes walking around on the street. One can simply, jump in the dumpster and start searching for this data and presto, you have sensitive information in hand.
So there you have it, some simple ideas and alternatives that you can use to find out sensitive information.
Please remember that performing ANY of these tasks could force you to face legal action from the company you are attempting to gain physical access to the dumpster or calling to find out information. So please do not perform these actions, unless you have permission. I am not responsible for any legal repercussions you may face for your actions.
Social engineering is simply making a phone call, knowing the right points of contacts and making sure you know what information you want. Kevin Mitnick was the famous hacker who used this method to gain usernames and passwords from people. http://en.wikipedia.org/wiki/Kevin_Mitnick
An example is as follows, a local IT member gets a call for a password reset from a person who is posing to work with the corporation. Now, because the company is so large, this IT person does not know everyone and cannot recognize their voice. Let's say this hacker starts a casual conversation with the IT person and starts talking about politics or the game that happened the night before. They could, also, say they need access to their account, immediately, for an important meeting. Once the IT person resets their password and lets them know it, then you have successfully gained access to an account you weren't supposed to have access to. Let's say they just reset it and never gave you the password, but you know through research that when they reset passwords it usually consists of some facets of their email address and something else you already know, which makes it easy to gain access to their password and account.
Many companies simply throw out information such as Health information or Military information in the trash. They don't shred this information or do anything to destroy this sensitive information. Some may even just dump it out back after they empty the office's trash cans. This leaves the data open and vulnerable to prying eyes walking around on the street. One can simply, jump in the dumpster and start searching for this data and presto, you have sensitive information in hand.
So there you have it, some simple ideas and alternatives that you can use to find out sensitive information.
Please remember that performing ANY of these tasks could force you to face legal action from the company you are attempting to gain physical access to the dumpster or calling to find out information. So please do not perform these actions, unless you have permission. I am not responsible for any legal repercussions you may face for your actions.
Sunday, February 23, 2014
Apple iOS 7.0.6's patch and the security flaw that prompted the patch
Let's consider a scenario where you need to connect to your bank via a website. How can you ensure that the communication link between you and your bank is secure?
Secure Sockets Layer (SSL) or the newer version of SSL: Transport Layer Security (TLS) is two encryption protocols that can be used to make sure that no third party is listening in on your conversation with your bank. When a communication between two entities IS intercepted, then we consider this a Man in the Middle Attack or MitM.
A MitM attack is where the Victim is communicating with the Web Server via an SSL connection. The attacker listens in on this communication and grabs all the sensitive data being transferred between the two connections. The Victim will have no idea that this is occurring.
The issue with iOS before 7.0.6 was that this SSL connection was not verified before the connection was created. So this created issues with MitM attacks. If you have an iPhone, then you should update as soon as possible. Currently, OS X does not have a patch for this, yet.
You can see the security flaw advisement posted on Apple's website here: http://support.apple.com/kb/HT6147
The description mentions:
Secure Sockets Layer (SSL) or the newer version of SSL: Transport Layer Security (TLS) is two encryption protocols that can be used to make sure that no third party is listening in on your conversation with your bank. When a communication between two entities IS intercepted, then we consider this a Man in the Middle Attack or MitM.
A MitM attack is where the Victim is communicating with the Web Server via an SSL connection. The attacker listens in on this communication and grabs all the sensitive data being transferred between the two connections. The Victim will have no idea that this is occurring.
The issue with iOS before 7.0.6 was that this SSL connection was not verified before the connection was created. So this created issues with MitM attacks. If you have an iPhone, then you should update as soon as possible. Currently, OS X does not have a patch for this, yet.
You can see the security flaw advisement posted on Apple's website here: http://support.apple.com/kb/HT6147
The description mentions:
iOS 7.0.6
- Data Security
- Available for: iPhone 4 and later, iPod touch (5th generation), iPad 2 and later
- Impact: An attacker with a privileged network position may capture or modify data in sessions protected by SSL/TLS
- Description: Secure Transport failed to validate the authenticity of the connection. This issue was addressed by restoring missing validation steps.
- CVE-ID
- CVE-2014-1266
Privileged network means that if you and the attacker are sitting at Barnes and Nobles together, then he/she can start sniffing your secure connections, which in the case of banking or any sensitive information is concerned, you don't want that.
You can see the function (highlighted below) where the issue occurs.
You can see the function (highlighted below) where the issue occurs.
static OSStatus
SSLVerifySignedServerKeyExchange(SSLContext *ctx, bool isRsa, SSLBuffer signedParams,
uint8_t *signature, UInt16 signatureLen)
{
OSStatus err;
SSLBuffer hashOut, hashCtx, clientRandom, serverRandom;
uint8_t hashes[SSL_SHA1_DIGEST_LEN + SSL_MD5_DIGEST_LEN];
SSLBuffer signedHashes;
uint8_t *dataToSign;
size_t dataToSignLen;
signedHashes.data = 0;
hashCtx.data = 0;
clientRandom.data = ctx->clientRandom;
clientRandom.length = SSL_CLIENT_SRVR_RAND_SIZE;
serverRandom.data = ctx->serverRandom;
serverRandom.length = SSL_CLIENT_SRVR_RAND_SIZE;
if(isRsa) {
/* skip this if signing with DSA */
dataToSign = hashes;
dataToSignLen = SSL_SHA1_DIGEST_LEN + SSL_MD5_DIGEST_LEN;
hashOut.data = hashes;
hashOut.length = SSL_MD5_DIGEST_LEN;
if ((err = ReadyHash(&SSLHashMD5, &hashCtx)) != 0)
goto fail;
if ((err = SSLHashMD5.update(&hashCtx, &clientRandom)) != 0)
goto fail;
if ((err = SSLHashMD5.update(&hashCtx, &serverRandom)) != 0)
goto fail;
if ((err = SSLHashMD5.update(&hashCtx, &signedParams)) != 0)
goto fail;
if ((err = SSLHashMD5.final(&hashCtx, &hashOut)) != 0)
goto fail;
}
else {
/* DSA, ECDSA - just use the SHA1 hash */
dataToSign = &hashes[SSL_MD5_DIGEST_LEN];
dataToSignLen = SSL_SHA1_DIGEST_LEN;
}
hashOut.data = hashes + SSL_MD5_DIGEST_LEN;
hashOut.length = SSL_SHA1_DIGEST_LEN;
if ((err = SSLFreeBuffer(&hashCtx)) != 0)
goto fail;
if ((err = ReadyHash(&SSLHashSHA1, &hashCtx)) != 0)
goto fail;
if ((err = SSLHashSHA1.update(&hashCtx, &clientRandom)) != 0)
goto fail;
if ((err = SSLHashSHA1.update(&hashCtx, &serverRandom)) != 0)
goto fail;
if ((err = SSLHashSHA1.update(&hashCtx, &signedParams)) != 0)
goto fail;
goto fail;
if ((err = SSLHashSHA1.final(&hashCtx, &hashOut)) != 0)
goto fail;
err = sslRawVerify(ctx,
ctx->peerPubKey,
dataToSign, /* plaintext */
dataToSignLen, /* plaintext length */
signature,
signatureLen);
if(err) {
sslErrorLog("SSLDecodeSignedServerKeyExchange: sslRawVerify "
"returned %d\n", (int)err);
goto fail;
}
fail:
SSLFreeBuffer(&signedHashes);
SSLFreeBuffer(&hashCtx);
return err;
}
SOURCE: http://opensource.apple.com/source/Security/Security-55471/libsecurity_ssl/lib/sslKeyExchange.c?txtHaving an extra "goto fail;" outside of an IF statement basically makes the rest of the code null and invalid. The code will execute all the way up to the IF statement, then execute the "go to fail;" statement and never makes it to the rest of the code. Apple argues that this code still takes care of MOST SSL connections, but when we are talking about sensitive information, you dont want something that works MOST of the time. You want something that works ALL the time.
Saturday, February 22, 2014
Wireshark at a glance
Wireshark or as it was formally known, Ethereal, is a tool that network administrators can use to sniff packets going across the wire. You can view many things from this perspective, such as login credentials going across the wire via clear text. You can also diagnose issues that may be occurring in your application your PC is running.
Wireshark gets installed in Promiscuous mode and this mode will allow you to sniff packets going across the network to and from any computer. (All traffic.)
In order for a network admin to stop this from happening is creating VLANs or Virtual Local Area Networks. By doing this, they can segment the network into many sub groups and separate them by routers. If this process is completed or exists in a network, then you can only sniff the traffic in your VLAN.
Go to the following link: http://www.wireshark.org/download.html in order to download Wireshark.
The installation screen will give you the below options.
Wireshark gets installed in Promiscuous mode and this mode will allow you to sniff packets going across the network to and from any computer. (All traffic.)
In order for a network admin to stop this from happening is creating VLANs or Virtual Local Area Networks. By doing this, they can segment the network into many sub groups and separate them by routers. If this process is completed or exists in a network, then you can only sniff the traffic in your VLAN.
Go to the following link: http://www.wireshark.org/download.html in order to download Wireshark.
The installation screen will give you the below options.
In order for Wireshark to work, you will need to install WinPcap. Allow it to do so, when prompted.
When Wireshark opens, you will see the below screen. You will need to select an interface to listen for traffic on. This option will be under the "Capture" section. Once you select an interface, you can click "Start" and you will start to see traffic.
This is what the next screen will look like. You will of course see many updates happening, which is all the traffic occurring on your network/PC. You can stop the capture by clicking the square red button. This will NOT clear the screen for you, but will allow you to analyze the data easier.
If you cannot figure out which interface is active, you can click the button under "File" and it will bring up a window that will help you determine which one is active.
In order to take Wireshark out of promiscuous mode, you can go to "Capture" and select "Options". This will bring up the below window and the circled area is the checkbox you can uncheck or verify that this mode is active.
Now you are ready to start sniffing traffic on your network!
Do not sniff traffic in public places you do not have permission to be sniffing data in. I am not responsible for ANY legal repercussions you can face for the misuse of this blog or product. This information is for educational purposes ONLY.
Labels:
ethereal,
network traffic analysis,
packet sniffing,
VLANs,
wireshark
Friday, February 21, 2014
Different types of Hacking
So what is hacking and how does it work?
First off, remember that anything that you learn in this blog is to be used ONLY for educational purposes and if you use this information for malicious purposes, you may face legal prosecution.
There are many different types of hackers, but lets first define what a "hacker" is. The media defines a "hacker" as someone who breaks into systems and steals data for their own greedy purpose.
In the hacking world, people who actually do this are called "crackers". They crack passwords and many other things. From this you can see how the name fits, but this world expands more than this.
We can classify these people into 3 categories:
- White hat
- Black hat
- Grey hat
White hat "hackers" are people who know have hacking skills and know how to exploit computers in the same fashion as "crackers", but their goal is to break into a system to better understand how to secure it.
Black hat "hackers" are people who break into a system to steal data and sell the data. These people may break into many different systems, deploy viruses, delete critical data and just flat out take out a service; they may cause havoc on a network.
Grey hat, these people are on the line of black and white. These members may use their skills for the side of good of helping other people out, but at the same time on another note use their skills to break into systems to steal data and resell it.
I just talked about these three terms in the global world as far as the terms go, but we can talk about these terms in the world of Penetration Testing or PenTesting. Corporations may hire people to test their network. A white hat person is greatly associated with this scenario, but grey hats are people who can also be hired. Grey hats in this scenario are people who know very little about the target network. Black hat members hired to perform a PenTest know nothing about the network.
When corporations hire these members, they need to have an established set of permissions and a Non-disclosure Agreement (NDA) signed with the hiring corporation. This means that when the hired hackers find data that could compromise a company's network, they can not share it with anyone, but the company. If they share it with an outside entity, then they may face legal repercussion.
Ethical hackers can be hired for this specific kind of testing. Ethical hackers need to follow protocol in order to provide a corporation with the necessary information they require about their network while maintaining a code of ethics.
With all of this being said, not everyone is out to get you and not all hackers are bad. Some are out there to help you. So just remember you don't have to be on the dark side in order to know cool stuff!
Thursday, February 20, 2014
A look into the world of Tor
Tor is a free tool that anyone can download, run and use to anonymize their internet activity. Think of Tor as in you talking to someone to get information about someone else. The person you are trying to get information about doesn't know you are getting information about them because they aren't answering your questions, but you still got the information you wanted.
In order to get Tor, go to: https://www.torproject.org/download/download
Once you run Tor, it will look like the below image. It will connect to the Tor network for you.
Once you have connected to the Tor network, FireFox will open up and tell you your IP address for the network. You can now start browsing the internet and not be traced!
The below image gives you a better idea of how Tor works. User 2 is trying to communicate with User 1. Let's say User 1 is a person or it can be a website. All User 2 has to do is connect to the Tor network and ask the network to fetch the website or a connection with User 1. Once Tor does this, they can bring you back the information you requested. Tor communicates with other Tor servers via an encrypted line so there is no trace that User 2 actually communicated to User 1.
Now these Tor routers or servers are usually PCs and these PCs can exist anywhere in the world! A person in the US can bounce their connection off a PC in Germany. This has its pros and cons though. The pro here is that it doesn't look like you are accessing the websites. The con is that it takes forever to bounce a signal off a machine halfway across the planet, to your destination and back to you.
Also note that in RED, this is an unencrypted line and any information you pass to your destination is completely visable. So you don't want to be logging into any servers.
Just remember that this information is NOT intended to be used for anything malicious and this information is for educational purposes ONLY. I am not responsible for any legal repercussions you face for your misguided actions conducted within Tor.
Labels:
anonymity,
anonymity network,
internet anonymity,
private,
proxies,
proxy,
Tor
Tuesday, February 18, 2014
Credit Card Numbers - In-depth analysis
Every day everyone uses a credit card to pay for many different things out there. Whether it be your normal bills, or going out to eat, but how do they work?
A good resource, even though it is Wikipedia, is: http://en.wikipedia.org/wiki/Bank_card_number
The first 6 digits help you identify the vendor of the credit card number. Depending on the vendor, it may only be up to 4.
The first digit of a credit card number is the Major Industry Identifier (MII). MII digits represent the following issuer categories:
In the old days, if you typed in your credit card number and purchased something online or provided your card over the phone, the manufacture would take up to a week to tell you the credit card number is wrong.
Now-a-days they can use an algorithm to validate the credit card number and tell you right away, before you even submit your card, that it is invalid. The algorithm is called the Luhn algorithm. This is the basic concept of how it works:
- How do websites know my credit card is valid?
- Do they have these numbers stored or do they pole credit card providers for the information?
A good resource, even though it is Wikipedia, is: http://en.wikipedia.org/wiki/Bank_card_number
The first 6 digits help you identify the vendor of the credit card number. Depending on the vendor, it may only be up to 4.
- 0 – ISO/TC 68 and other future industry assignments
- 1 – Airlines
- 2 – Airlines and other future industry assignments
- 3 – Travel and entertainment and banking/finance
- 4 – Banking and finance
- 5 – Banking and finance
- 6 – Merchandising and banking/finance
- 7 – Petroleum and other future industry assignments
- 8 – Healthcare, telecommunications and other future industry assignments
- 9 – National assignment
In the old days, if you typed in your credit card number and purchased something online or provided your card over the phone, the manufacture would take up to a week to tell you the credit card number is wrong.
Now-a-days they can use an algorithm to validate the credit card number and tell you right away, before you even submit your card, that it is invalid. The algorithm is called the Luhn algorithm. This is the basic concept of how it works:
- From the rightmost digit, which is the check digit, moving left, double the value of every second digit; if the product of this doubling operation is greater than 9, then sum the digits of the products.
- Take the sum of all the digits.
- If the total modulo 10 is equal to 0 (if the total ends in a zero) then the number is valid according to the Luhn formula; else it is not valid.
Since we like to focus on C#, I will post a C# implementation of the Luhn algorithm at a later time.
Monday, February 17, 2014
Vulnerability scanning using Linux and Nessus.
Today we will be talking about Vulnerability scanning. Do NOT perform these scans on a network you do not have permission to do so on. This is for educational purposes ONLY. It is not my responsibility if you are scanning a network you shouldn't be scanning. Always get permission FIRST before you perform any of the below items. If you scan a network you do not have permission to scan you can get into serious trouble and may even face legal action.
The first item you will need is Virtual Box. We are using Virtual Box to allow us to virtualize 2 machines here: a host machine and a target machine. Virtual Box is free compared to VMWare, so it is preferred. In order to get your copy of VBox, go here: https://www.virtualbox.org/wiki/Downloads
Download the appropriate version for your Operating System (OS).
Next, you will need BackBox or any equivalent Linux flavor. Perform the steps below in order to get BackBox, but first go to the website and download the appropriate version you would like: http://www.backbox.org/downloads
VBox will start up looking like the below image. You just need to click "New" from here.
It will ask you the Name, Type and Version. Enter the below data and give it a name.
Next is memory, you will want to give it a significant amount of memory so it can perform things in a quick manner. The more the better, but up 4 GB should be good enough.
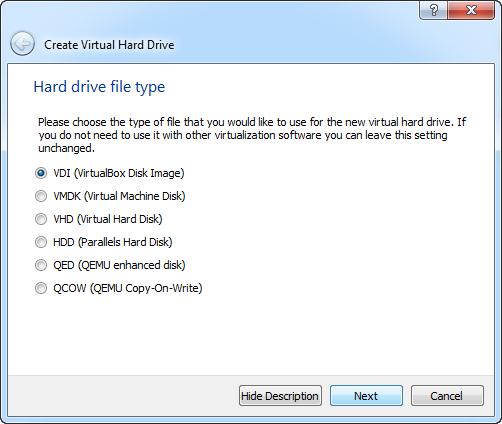
It will ask what format do you want to slice the Physical Hard Drive into. I usually do it in a VDI format, but VMDK will work, too. (any really)
Make sure you enter it as "Fixed Size" or the hard drive will grow based on the needs of the OS and if your Virtual Box gets too cluttered, it will eat up the Host's space. We don't want that!
Here is where you select the size, remember I stated 20 GB is good.
Below is what you will see as it creates this new HDD.
Once you create this HDD, when you create NEW machines later on, you can attach this HDD to other Virtual Machines as it will prompt you here below:
Before you boot BackBox, make sure you have the image you downloaded from the website set to the disc shown in the picture below. If you only have the .vdi (the virtual Hard Drive) and now disk, then you will be essentially booting a blank Hard Drive. Click the disk or in this case "Empty" and on the right under "Attributes" you can select a disk or image to have mounted in your virtual tray when you boot.
Once you boot from the image and you have your Virtual Hard Drive ready to go, you will see the below screen. Go ahead and hit enter on "Try BackBox without installing"
Once it completes, you have Back Box installed and you are ready to go!
If you want to burn a disk and install BackBox this way, then here are the instructions:
Make sure that your computer is set to boot from the cd drive.
- Insert the BackBox disc into your CD drive.
- Start or restart your computer.
- Select "Try BackBox without installing"
- Click "Install BackBox Linux". The "Language" screen appears.
- Select your desired language and click "Forward"
- Select the location closest to your location and click "Forward".
- Select where do you want to put BackBox and click "Forward".
- Enter the requested information, and click "Forward". The "Ready to install" window appears.
- Verify that the language, layout, location, and personal information are correct and click "Install". The installation wizard begins.
- When the installation wizard finishes, the "Installation complete" window appears.
- Click "Restart now" to restart your computer. BackBox is now installed!
- Getting VirualBox Guest Addons to work: http://www.dedoimedo.com/computers/virtualbox-guest-addons.html
Installing Metasploitable and getting it up and running: https://community.rapid7.com/message/4137#4137
Installing Nessus: http://uwnthesis.wordpress.com/2013/07/31/kali-how-to-install-nessus-on-kali/
Once you download Nessus, you just need to run it:
Once you have ran the debian and Nessus is installed. You just need to start the service and browse to the website: https://127.0.0.1:8834 to configure Nessus.
You're now ready to start scanning Metasploitable 2!
Disclaimer: I am not responsible for any damage or any malfunctions that may occur during the process of installing this application and use.
Labels:
BackBox,
Linux,
Metasploit,
Metasploitable,
Nessus,
VirtualBox,
Vulnerability scanning
Sunday, February 16, 2014
Scripting with Microsoft's PowerShell - Advanced
Lets sharpen our PowerShell scripting skills. Today we will be looking at a script and going through it. Here is the script:
- write-host
- write-host "Which option would you like:"
- write-host 1: "Choice 1"
- write-host 2: "Choice 2"
- write-host 3: "Choice 3"
- write-host 4: "Choice 4"
- write-host 5: "Exit."
- $userinput = [Console]::ReadLine()
- Function switchUserInput ($userinput)
- {
- switch ($userinput)
- {
- 1 {write-host "You chose option 1"}
- 2 {write-host "You chose option 2"}
- 3 {write-host "You chose option 3"}
- 4 {write-host "You chose option 4"}
- 5 {exit}
- default {"You must enter a number between 1 and 5"}
- }
- }
- switchUserInput($userinput)
Line 24 calls a function that is defined on line 11. We need to define the function we want to use before we use it so we defined it first here. The function is called "switchUserInput" and it takes a variable named "$userinput". Once the function is called and ran, it puts the variable inside a Switch statement. Based on the value of what $userinput is, it executes the command. You can have it written to the screen or have it execute another function.
The below image is what the script looks like when ran:
In order to make this script slightly better, we can make it so the user has to exit the script instead of auto-exiting.
In order to do this, we just have to expand the function. Add this after the switch statement:
- write-host "Would you like to return to main menu?"
- $choice = [Console]::ReadLine()
- if(($choice.ToLower() -eq "yes") -or ($choice.ToLower() -eq "y"))
- {
- write-host
- write-host "Which option would you like:"
- write-host 1: "System related."
- write-host 2: "Group related."
- write-host 3: "Server task related."
- write-host 4: "Query related."
- write-host 5: "Exit."
- $mainMenuReturn = [Console]::ReadLine()
- switchUserInput($mainMenuReturn)
- }
- elseif (($choice.ToLower() -eq "no") -or ($choice.ToLower() -eq "n"))
- {
- exit
- }
- else
- {
- write-host
- write-host "You did not enter a valid option."
- write-host "Main menu: "
- write-host
- write-host "Which option would you like:"
- write-host 1: "System related."
- write-host 2: "Group related."
- write-host 3: "Server task related."
- write-host 4: "Query related."
- write-host 5: "Exit."
- $mainMenuReturn = [Console]::ReadLine()
- switchUserInput($mainMenuReturn)
- }
So line 1 we ask them if they want to return to the main menu, then line 2 we wait for their input and store it in a variable named "$choice". We then have an IF statement testing what they entered. We do not want to be case sensitive here so we convert their answer TOLOWER. If they entered "yes" or "y”, then we post the choices again in lines 5 through 11. We then wait for their answer and store it in "$mainMenuReturn". We then call our function: "switchUserInput" and pass it the appropriate variable.
If the user enters "no" or "n", then we simply exit the script.
If they enter something besides "yes", "y", "no" or "n", then we wait to tell them that they entered the wrong choice and repeat the choices for them.
Now our script is complete! We can now provide a menu of choices for the user and recursively run until the user does not want the script running anymore.
Scripting with Microsoft's PowerShell - Beginner
We will be taking a step into the world of scripting with PowerShell. PowerShell scripts file extension end with ".ps". They are normal text documents and can be edited in any text editor.
Here are some instructions on creating and writing your Hello World for PowerShell
If you are running PowerShell for the first time, you may see this:
If you see this error, this means that you have unsigned PowerShell scripts set to restricted or as in they cannot run. In order to check this, type: "GET-ExecutionPolicy".
If it returns "Restricted", then this means you need to change the Execution Policy.
In order to do this, type "SET-ExecutionPolicy remotesigned". Before you do this, you will need to re-open PowerShell with Administrative Privileges.
Once again check to see what the policy is by typing: "GET-ExecutionPolicy". Verify it does not say "Restricted".
In order to return the settings back to the original settings, simply type: "SET-ExecutionPolicy restricted"
Congratulations, you just wrote your first PowerShell script!
Here are some instructions on creating and writing your Hello World for PowerShell
- Create a text file and name it "Hello.ps1"
- Open up this file in a text editor of your choosing.
- Write inside of this text file: "write-host "Hello World.""
- Open up PowerShell
- Make sure your default location is set to the same folder of the location of the file. You can also drag and drop the file to your PowerShell window and press enter.
- Once the command runs, you will see it write Hello World.
If you are running PowerShell for the first time, you may see this:
If it returns "Restricted", then this means you need to change the Execution Policy.
Once again check to see what the policy is by typing: "GET-ExecutionPolicy". Verify it does not say "Restricted".
In order to return the settings back to the original settings, simply type: "SET-ExecutionPolicy restricted"
Congratulations, you just wrote your first PowerShell script!
Saturday, February 15, 2014
Basics of Microsoft's PowerShell
Window's PowerShell (PS) is Microsoft's task automation and configuration management framework, consisting of a command-line shell and associated scripting language built on .NET Framework. Today I will be going over a few basic commands you can run immediately to get you going into exploring the full capabilities of PS.
Starting with the GET commands try going to the Start pearl in the lower left hand corner of Windows 7 and in the search bar type in "Power Shell". Once it is up and running, you can type in "GET-ACL". ACL stands for Access Control List.
The next simple command is just to get the date. Type in "GET-DATE". Now this may seem like a simple function that serves no real use, but when you start writing scripts and you want the script to perform a particular action at a certain time, you'll need to call this function and store the data, then write an IF/ELSE statement to handle it. This gives you more control over your Operating System and within your Script.
If you are unsure on what commands are available or need help, you can type "GET-HELP".
Instead of using Windows Task Manager which lists all the currently running processes, you can run "GET-PROCESS" to dump a listing of currently running processes and you can save this data in a text file. In your script, you can say something of the nature of "IF problem GET-PROCESS". This is, of course, pseudocode.
I did not jump into the scripting capabilities, yet. I will have another posting for diving into the scripting facet.
The next simple command is just to get the date. Type in "GET-DATE". Now this may seem like a simple function that serves no real use, but when you start writing scripts and you want the script to perform a particular action at a certain time, you'll need to call this function and store the data, then write an IF/ELSE statement to handle it. This gives you more control over your Operating System and within your Script.
If you are unsure on what commands are available or need help, you can type "GET-HELP".
If you would like a full listing of a specific kind of command, you can use regular expression within GET-HELP. You can type something such as "GET-HELP-Name Get-*" and this will dump out a full listing of all Get commands.
Just like dumping out what the currently running processes are, you can also dump out the currently running services and their current state. Use the command "GET-SERVICE" to get a listing of this.
A deep dive into Excel 2010's ribbon menu
Introduced in Microsoft's Office 2010, the ribbon was designed to provide a quicker and easier interface for the buttons. I will talk about a few of the home buttons on the ribbon. Under this tab you can perform some of the more commonly used functions such as format the text, formulas, pasting data and formatting tables.
Under the Number menu we can change how the cell shows our data. We can set the numbers as such things as "Percentage" or "Fraction". You can change the dollar amounts to Euros or other currency. Finally, you can increase or decrease the number of decimals the numbers show.
The Styles section allows you to change a cell or cells so that they can have a colored scheme to them. They make the cells easier to read and allow you to be more organized with your data. You can also format the data as a table and choose your layout.
The Cells section allows you to insert cells, delete cells or format them. You can select such items as listed in the picture below.
The last item on the ribbon is Editing. From here you can use formulas to be inserted into a cell, Fill a cell or Clear it. You can also apply a filter to sort your columns. Find & Select allows you to search for data you may be looking for. You can also press the hotkey of Control+F.
Subscribe to:
Comments (Atom)